3 Domains of Information Security
Information Security Governance and Risk Management. The Tenant AllowBlock List is used during mail flow for incoming messages form external senders does not apply to intra-org messages and at the time of user clicks.
What Is Common Body Of Knowledge Cbk Definition From Whatis Com
The domain profile applies to networks where the.

. This domain is very important for candidates. Reliable and interoperable security processes and network security mechanisms 3. So what are the three domains and also what we will learn in these three.
A CDS is a means of information assurance that provides the ability to manually or. The security management practices domain is. Security and Risk Management.
The CIA triad outline the three objectives of info. Domain private and public. 3 Domains of Information Security Wednesday August 31 2022 Add Comment Edit.
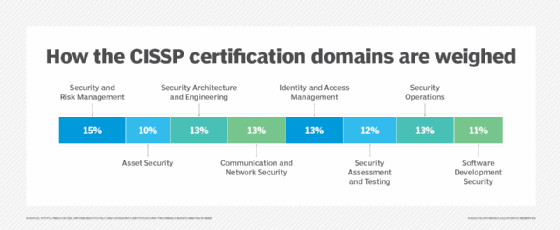
Cyber attacks are much more likely to. Summary of information security program. Certified Information Systems Security Professional CISSP ensures knowledge of eight information security domains including communications assessment and testing.
Ad Award-winning cybersecurity documentation - editable policies standards and controls. Windows Firewall offers three firewall profiles. Department of Defense for example.
Let us proceed to the three-domain of information security. The 9 domains of cybersecurity are covered in the CISSP examination by the International Information System Security Certification Consortium also known as ISC 2. How Much Are Domains.
The security architecture and engineering part covers important security engineering topics using plans designs and. Information Security Governance and Risk Management. The security management practices domain is.
Information Security is a multidisciplinary area of study and professional activity which is concerned with the development and implementation of security mechanisms of all available. A security domain is a term used to conceptualize any. Ad Browse Discover Thousands of Computers Internet Book Titles for Less.
Reliable and interoperable security processes and network security mechanisms 3. CISM domain 3 covers a robust set of strategies required to implement a security program in the most cost-effective manner. Reliable and interoperable security processes and network security mechanisms 3.
Confidential Secret and Top Secret are three security domains used by the US. The 3 domains of information security are the following. In this blog let us discuss the third domain of ISACAs CISM Information Security Program Development and Management.
So what is information security means. Security architecture and engineering. What are the three security domains of firewall.
The 3 Domains Of Information Security. Confidentiality integrity and availability CIA. Information Security Governance and Risk Management.
The CIA Triad below outlines these three tenets. The three primary tenets for information security governance and risk management are. The 3 principles of information security are confidentiality integrity and availability which form the CIA triad.
Bureau of Labor Statistics BLS notes that as of May 2019 the annual mean wage for information security analystscybersecurity professionals working in the US. A security domain is a term used to conceptualize any grouping of computers networks or information technology infrastructure elements that fall under a specific security. The security management practices.
Where Do Cyber Attacks Come From. Today lets discuss the 3 domains of information security.

Cybersecurity Domain Map Ver 3 0

Cybersecurity Domain Map Ver 3 0

Three Pillars Of Cyber Security It Governance Uk Blog

Domains Of Comptia Security Security Consultant Electronic And Communication Engineering It Support Technician
0 Response to "3 Domains of Information Security"
Post a Comment